Uncovering Trickbot's use of IoT devices in command-and-control infrastructure | Microsoft Security Blog
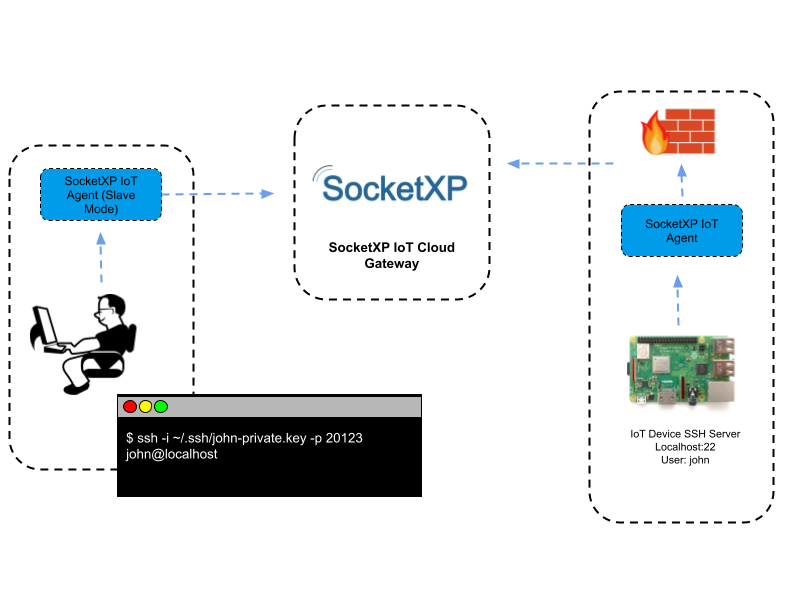
Remote SSH into IoT devices or Raspberry Pi behind NAT router or firewall from outside network over the internet | by Ganesh Velrajan | Medium