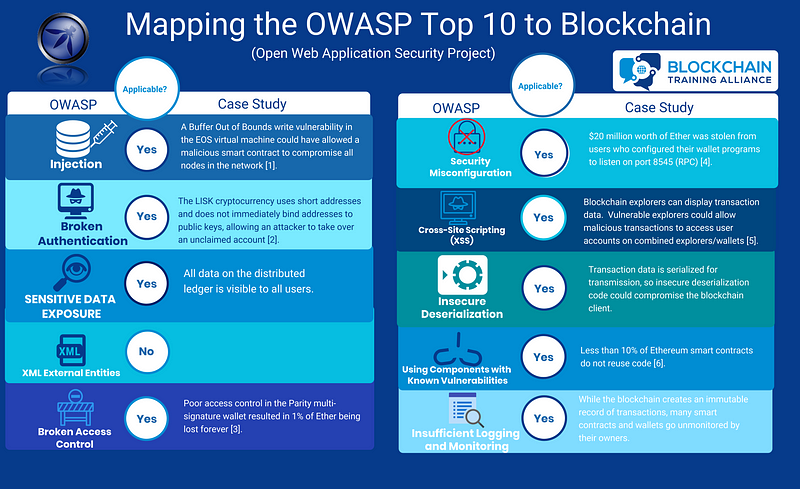
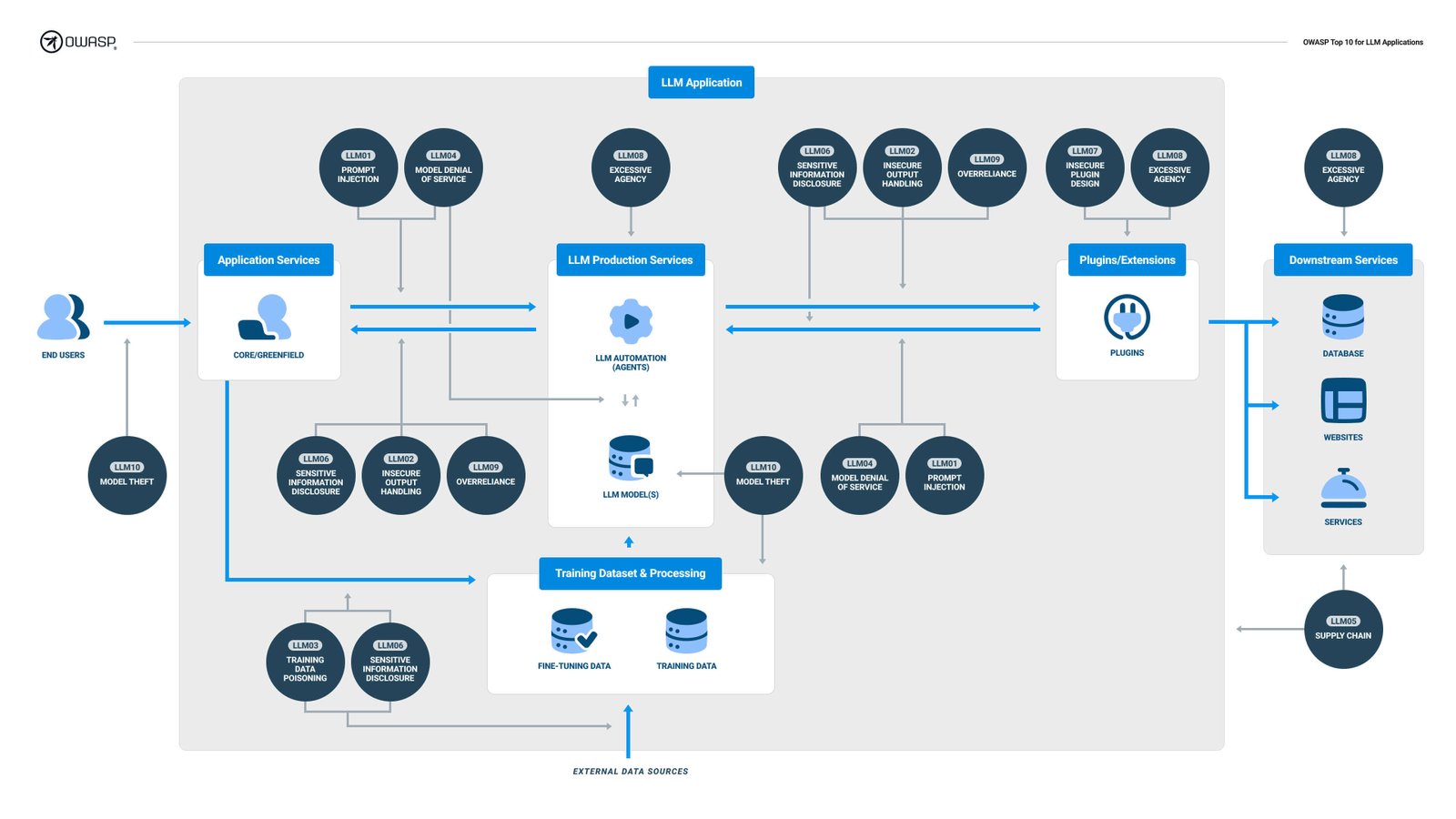
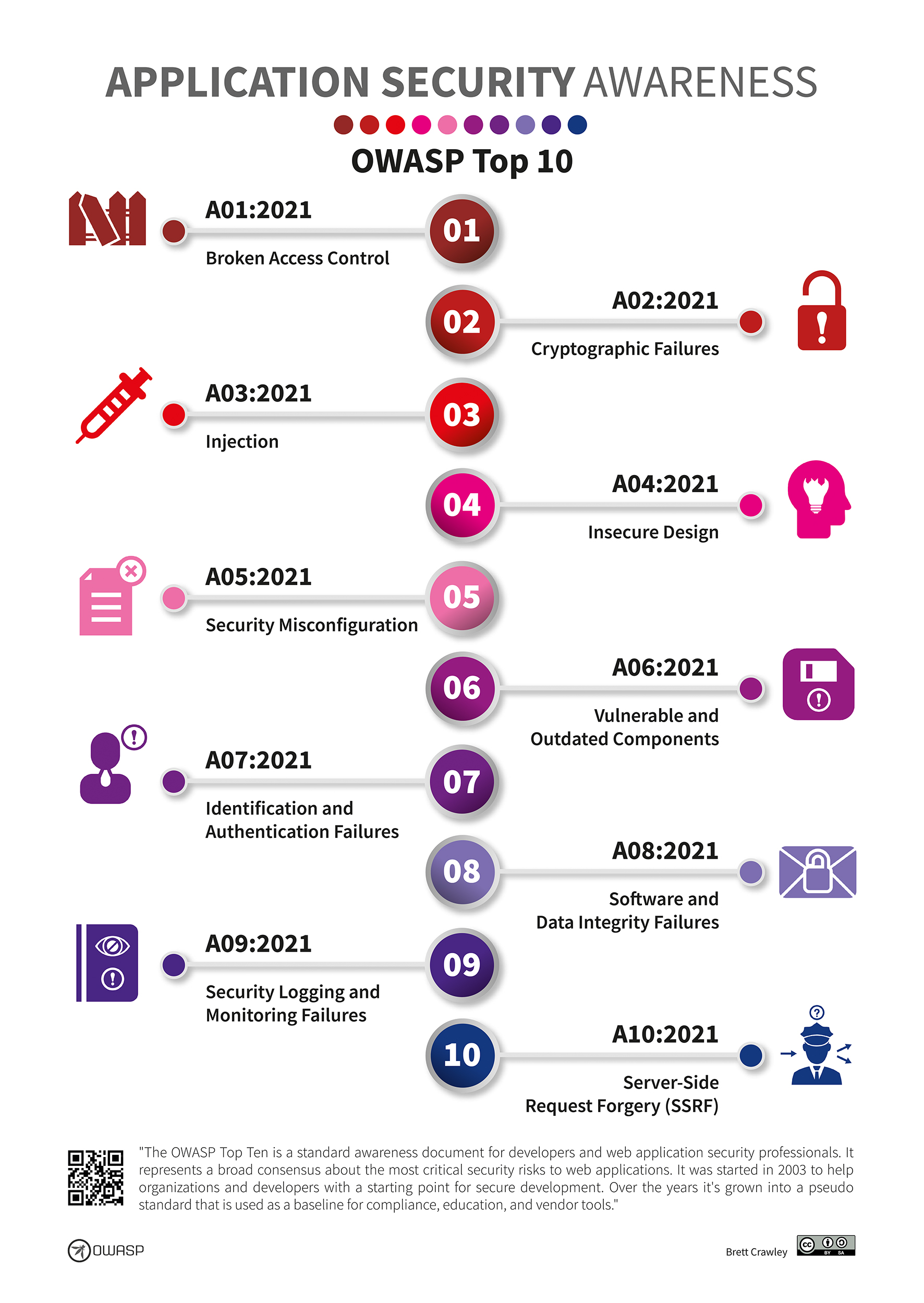
OWASP Top 10 for Large Language Model Applications Explained: A Practical Guide | Lakera – Protecting AI teams that disrupt the world.
GitHub - romanzaikin/Owasp-TOP-10-Training-Panel: This repository contains the source code of the web panel I have used in my book series of books: Cyber and Penetration Testing – Web Penetration Testing.







![Web hacking training [hands-on] - YouTube Web hacking training [hands-on] - YouTube](https://i.ytimg.com/vi/-vXUhAqvs6M/hqdefault.jpg)