Apriorit on X: "Hackers often leverage sophisticated methods to compromise applications on all platforms💻📲 Heap spraying attacks are one of such methods. This method allows attackers to exploit vulnerabilities in applications and

What is the heap spraying technique and how does it work? | by Apriorit | Apriorit — Specialized Software Development Company | Jan, 2024 | Medium
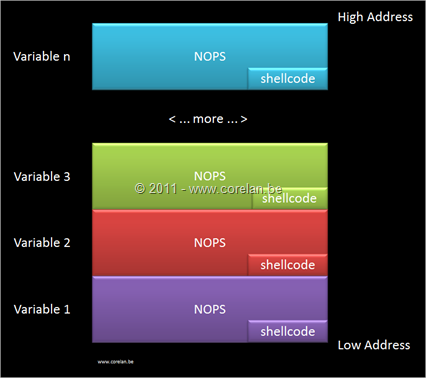
Exploit writing tutorial part 11 : Heap Spraying Demystified | Corelan Cybersecurity ResearchCorelan Cybersecurity Research

Apriorit on X: "Hackers often leverage sophisticated methods to compromise applications on all platforms💻📲 Heap spraying attacks are one of such methods. This method allows attackers to exploit vulnerabilities in applications and

PPT - Nozzle: A Defense Against Heap-spraying Code Injection Attacks PowerPoint Presentation - ID:2510980

Project Zero: Remote iPhone Exploitation Part 2: Bringing Light into the Darkness -- a Remote ASLR Bypass

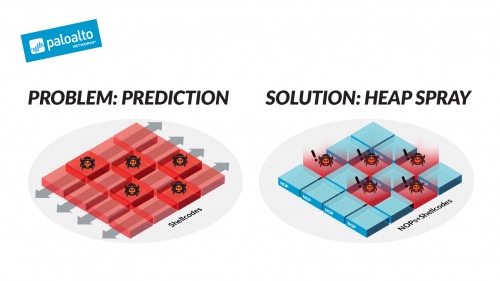








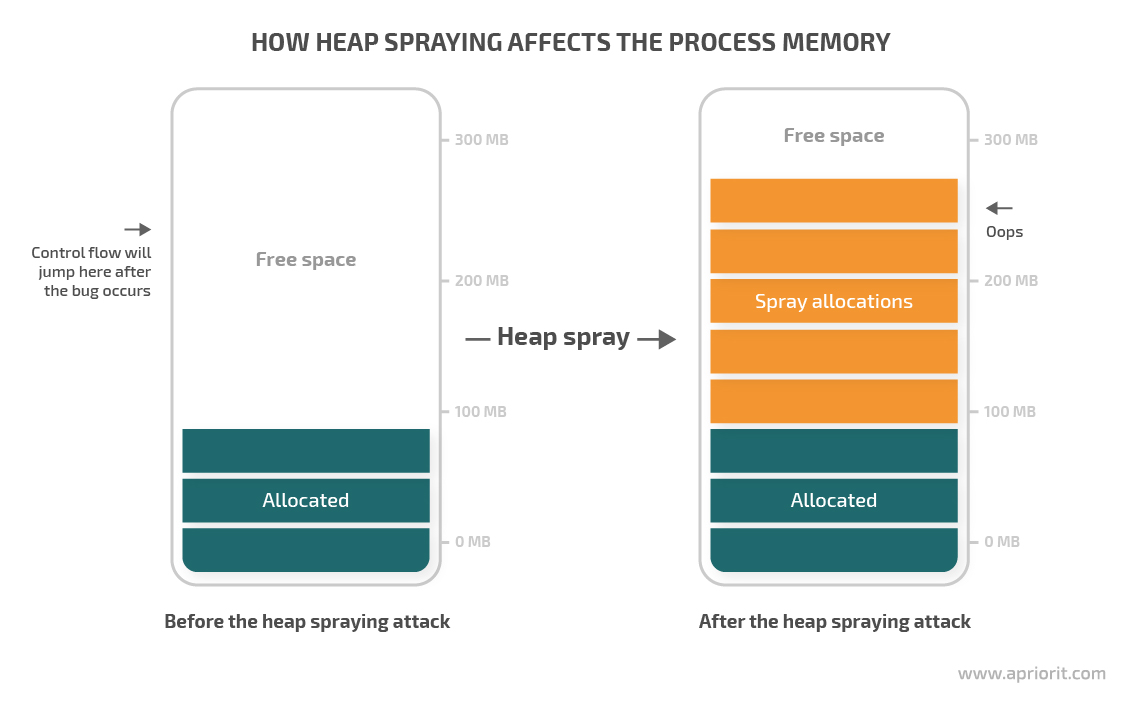

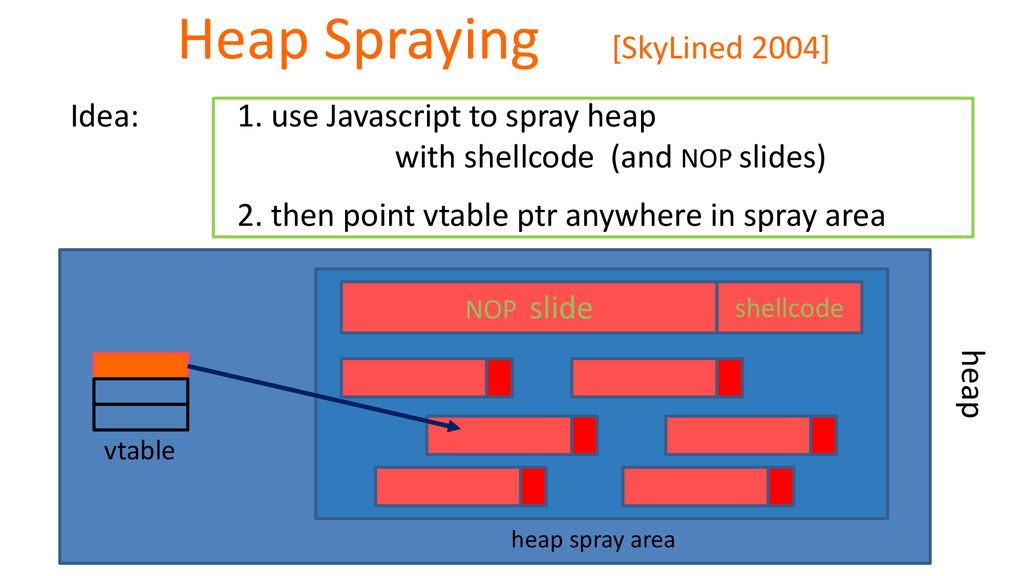
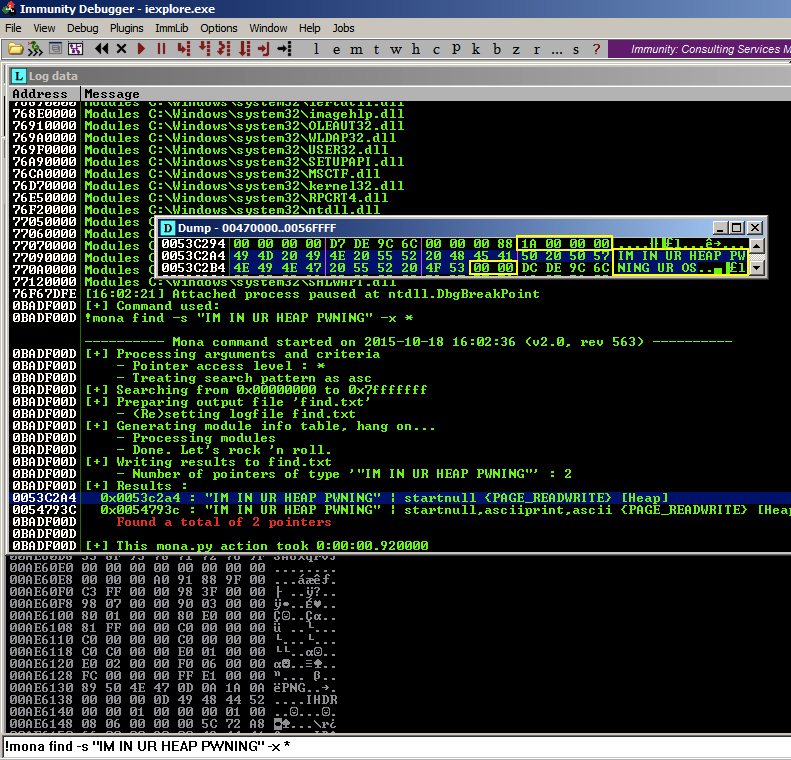

![PDF] NOZZLE: A Defense Against Heap-spraying Code Injection Attacks | Semantic Scholar PDF] NOZZLE: A Defense Against Heap-spraying Code Injection Attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/24b2f987c6a1b633df3a8ca970ce59a7259fd482/3-Figure1-1.png)